THE BLOG
In my latest training video, I cover the theory of Open Shortest Path First (OSPF) routing protocol.
OSPF is the most popular interior gateway protocol used today. In this...
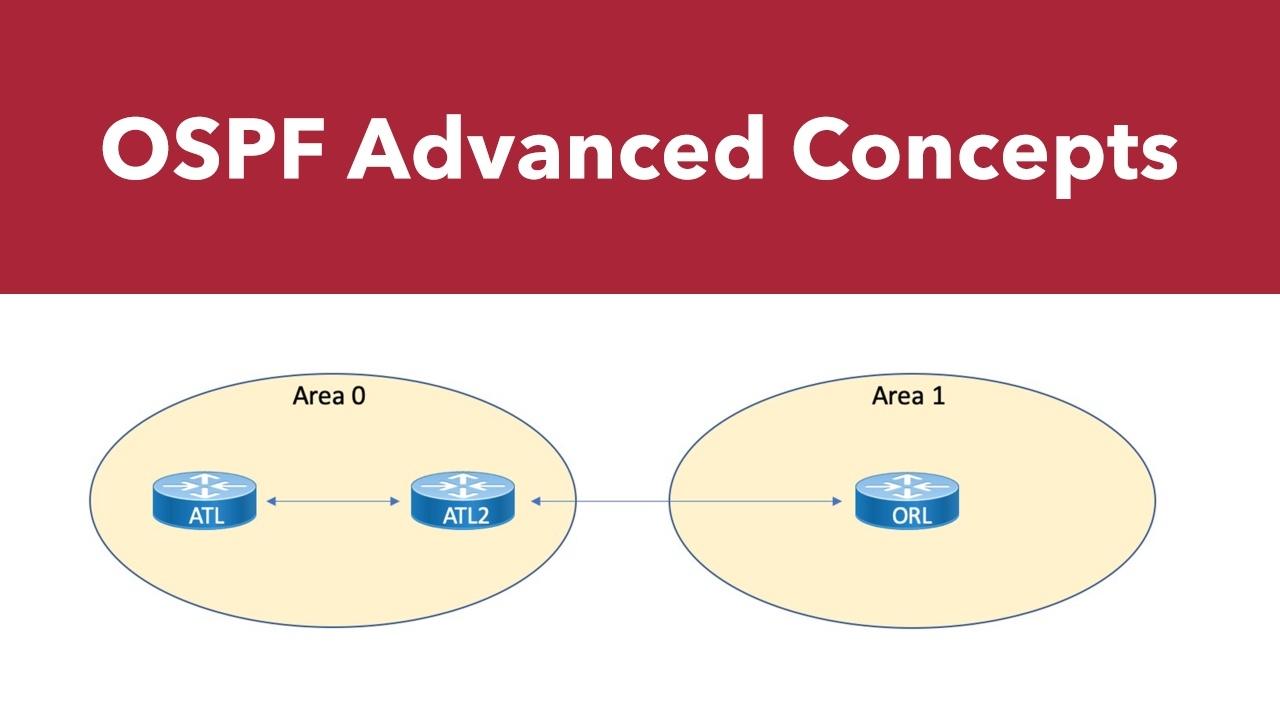
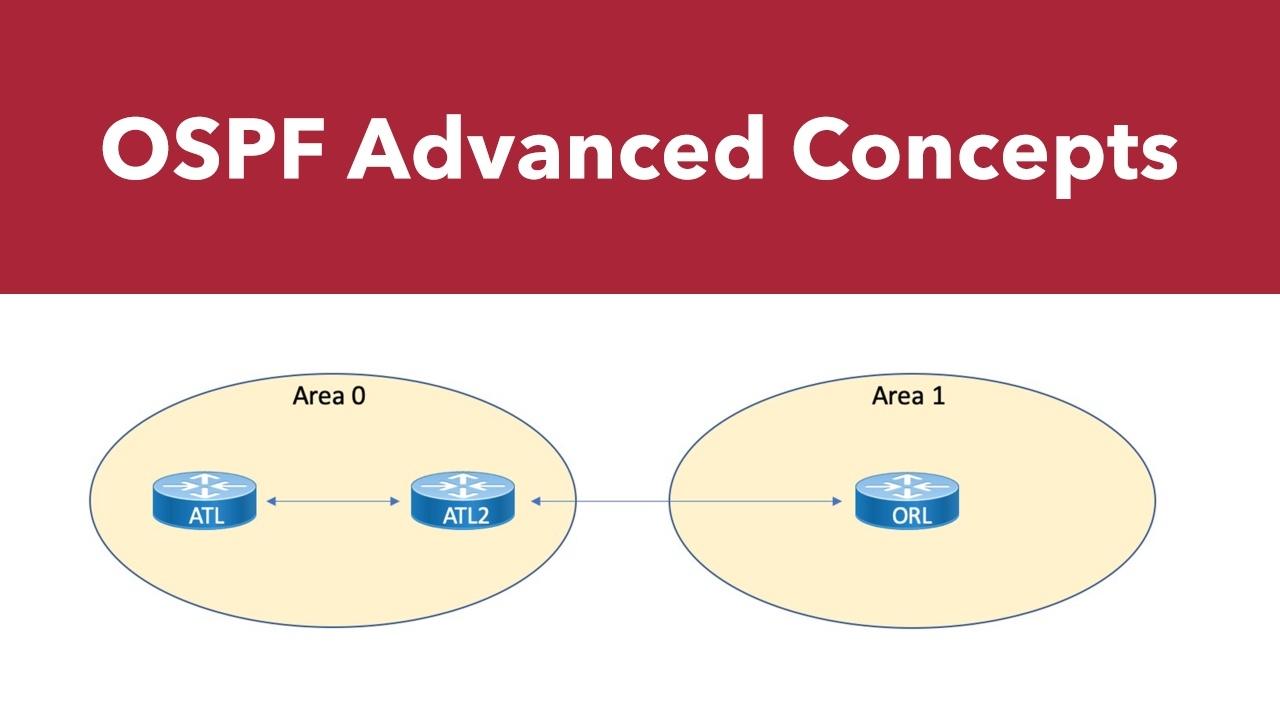
In the previous part of our OSPF series, we examined options for manually filtering routes. As we wrap up our look at advanced OSPF topics, we'll discuss default routes, and compare OSPFv2...
In our previous blog post, we examined how OSPF can automatically filter routes through the use of special areas and LSA Types. But what about your options for manually filtering...
Last time, we began our look at advanced OSPF topics with the configuration of backbone and non-backbone areas. In this blog post, we'll look at the creation of more specific area types.
Stubby...
The time has arrived to tackle some of the more advanced (and interesting) features of the Open Shortest Path First routing protocol. We begin by examining the configuration and verification of the...
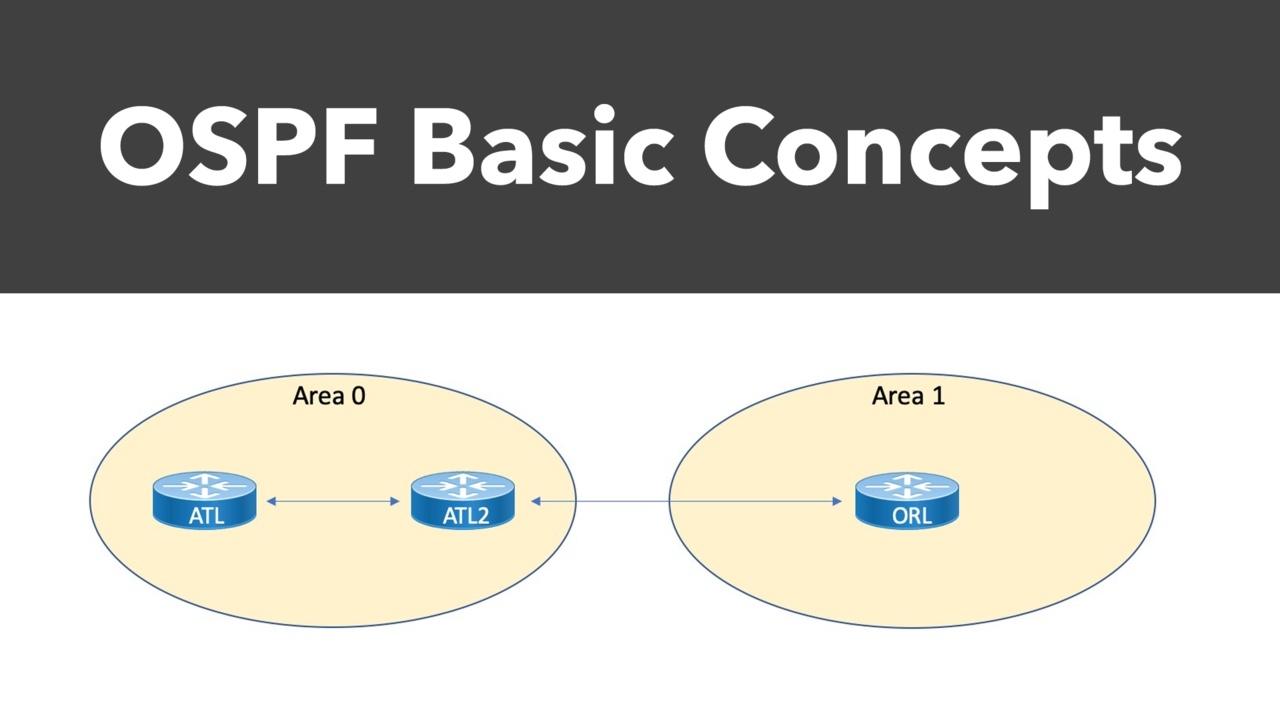
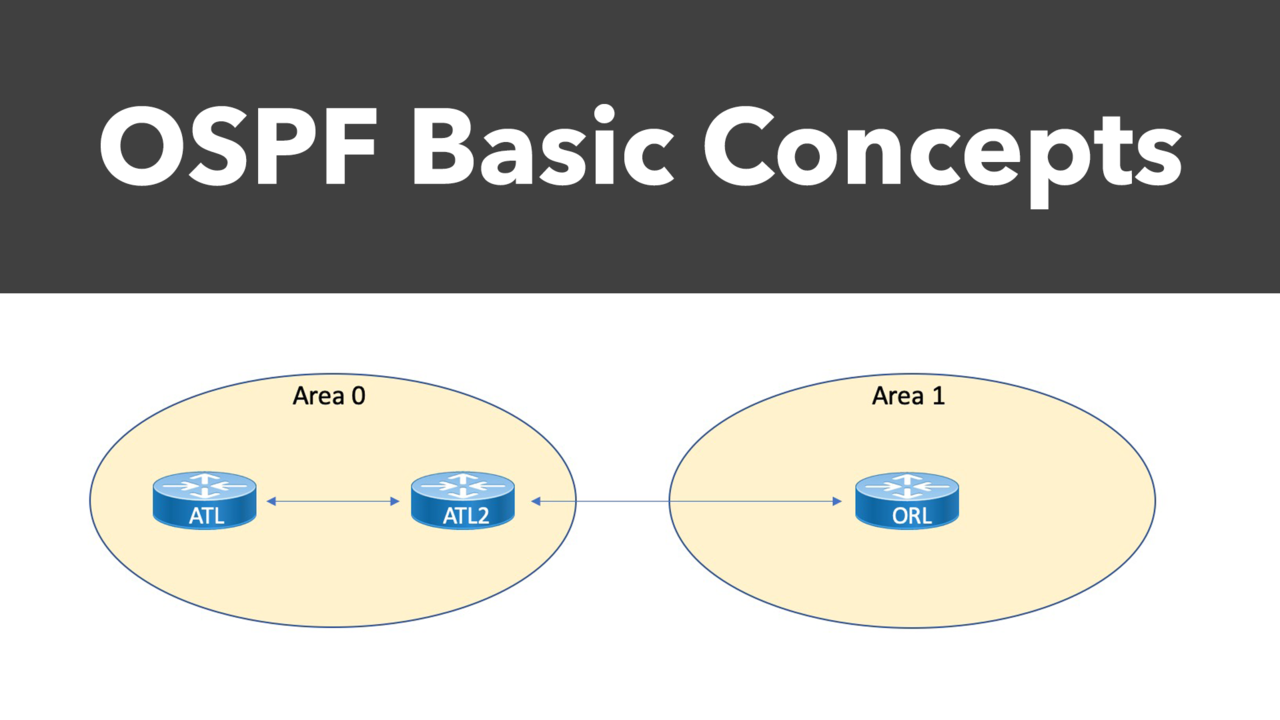
Before we move on to more advanced topics, we'll wrap up this OSPF Basics series in Part 3. Here we'll examine LSA types, area types, and virtual links.
OSPF LSA Types
Link State Advertisements...
In the previous blog post, we looked at a few fundamental OSPF concepts, including neighbor and adjacency formation. As we continue through the basics of OSPF, this post will examine...
The OpenShortest Path First (OSPF) dynamic routing protocol is one of the most beloved inventions in all of networking, widely adopted as the Interior Gateway Protocol (IGP) of choice for many...
On Monday June 10, 2019 Cisco announced an unprecedented revamp of their certification program. This post dives into one of the major updates, the new CCNA certification. (We'll have a future blog...
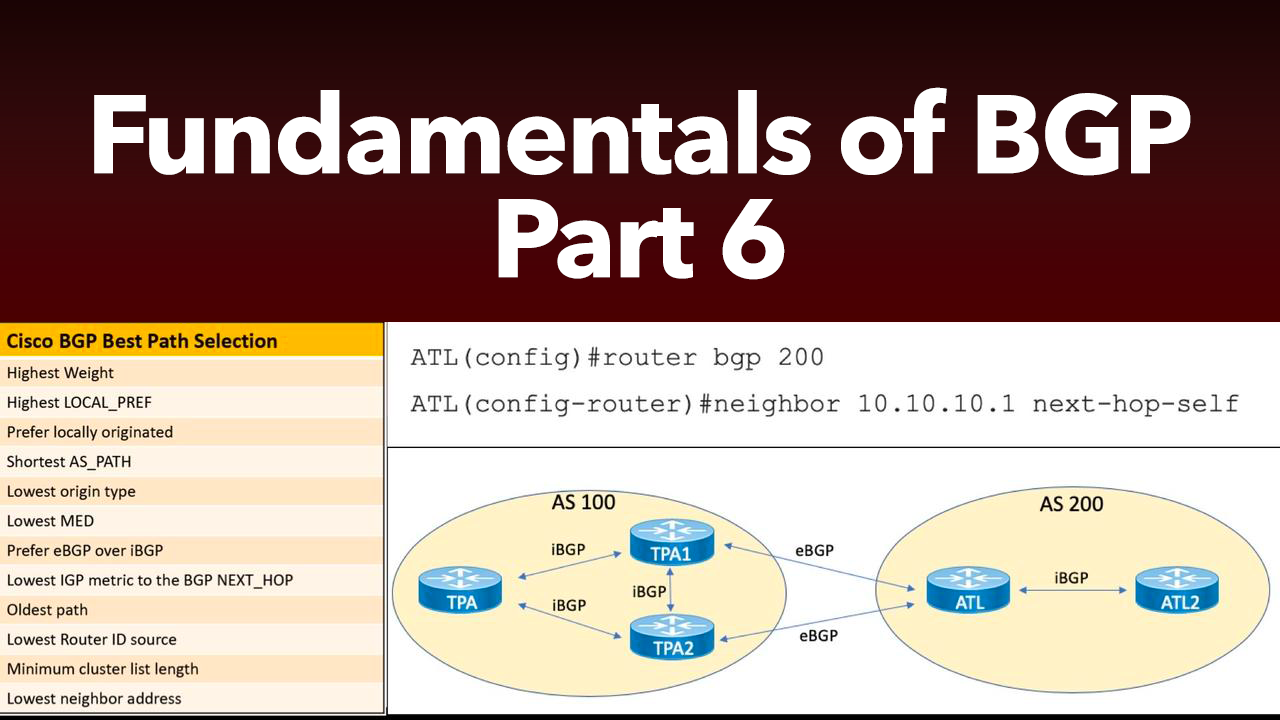
This post is the 6th and final in a series of Border Gateway Protocol (BGP) posts. If you missed any of the first five parts, here are the links:
This post is the 5th in a series of Border Gateway Protocol (BGP) posts. If you missed any of the first four, here are the links:
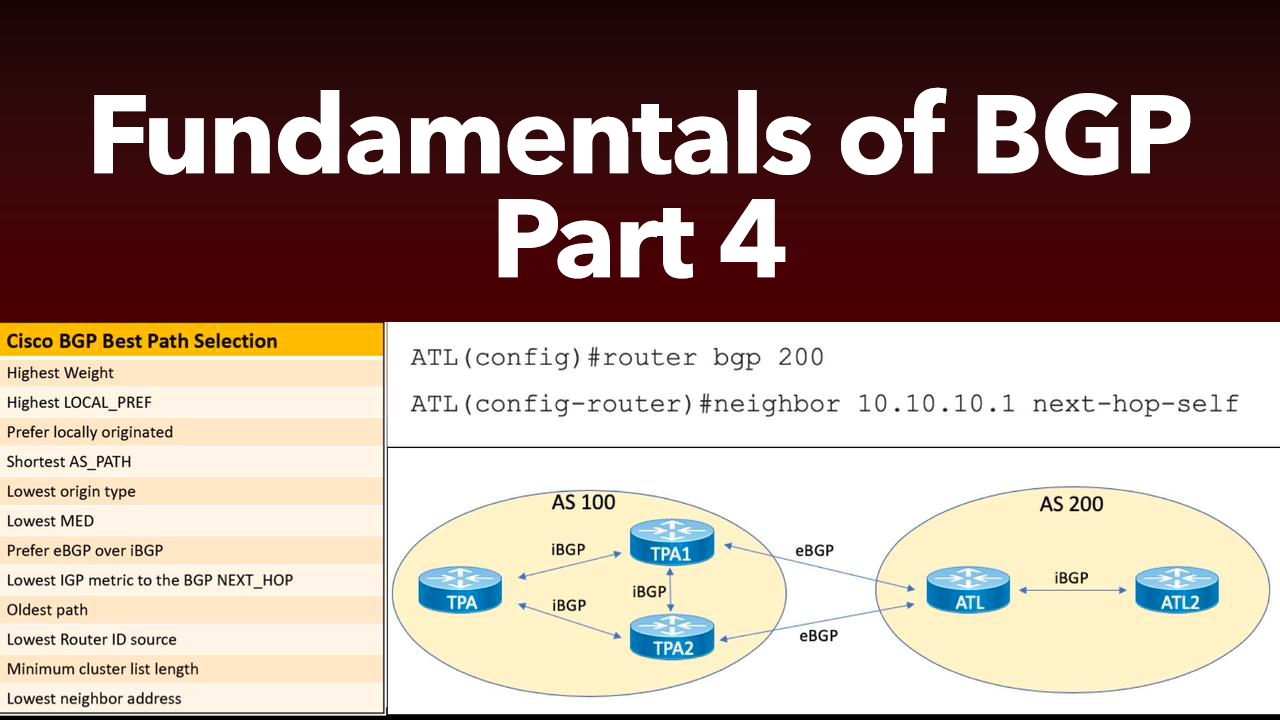
This post is the 4th in a series of Border Gateway Protocol (BGP) posts. If you missed any of the first three, here are the links:
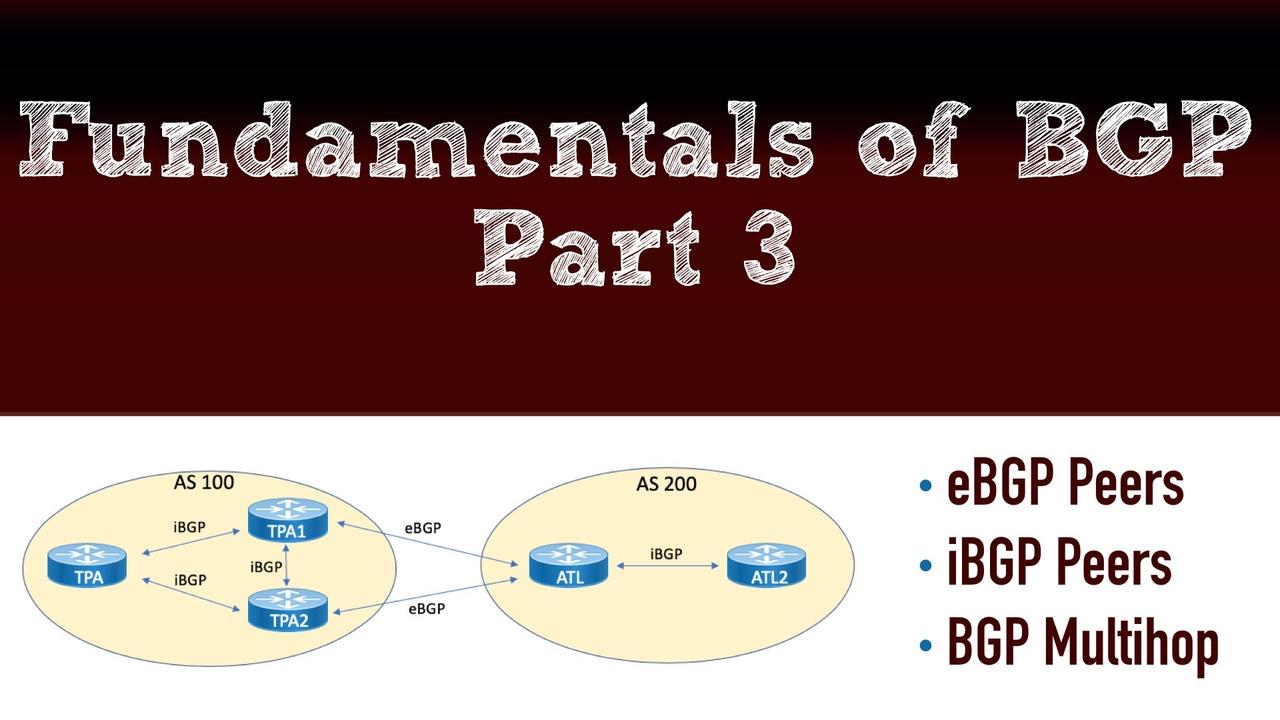
This post is the 3rd in a series of Border Gateway Protocol (BGP) posts. If you missed either of the first two, here are the links:
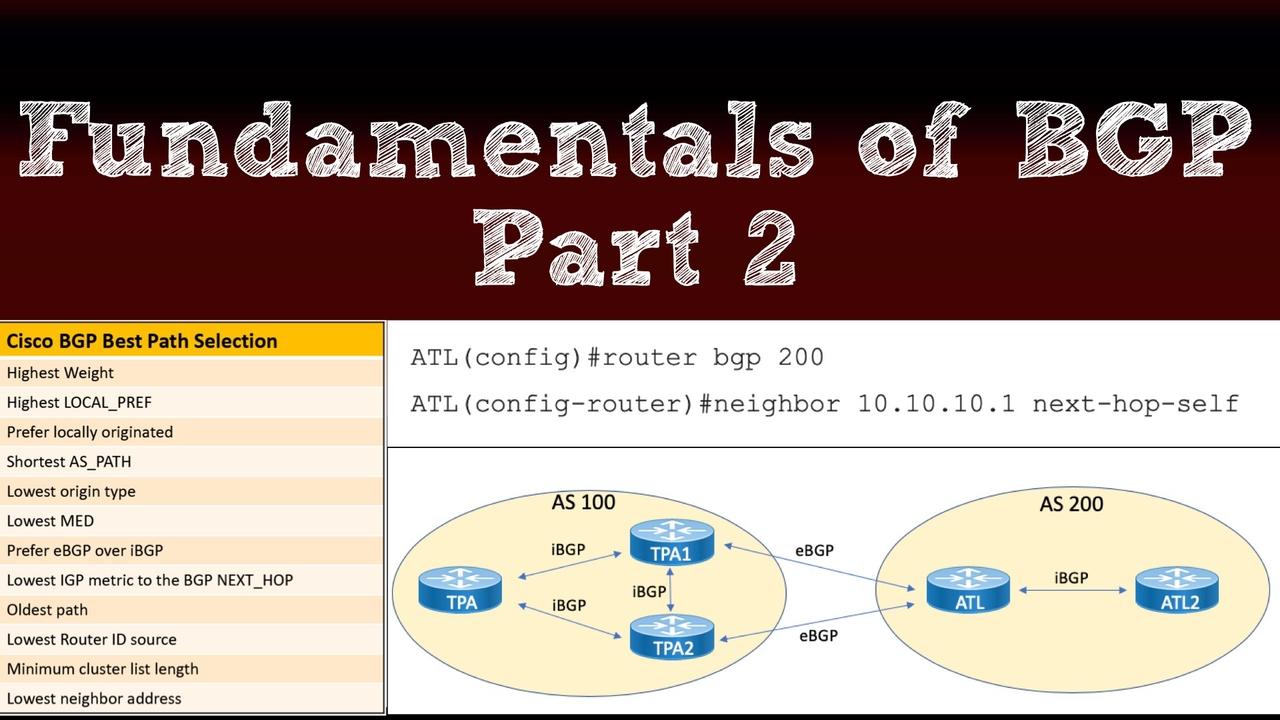
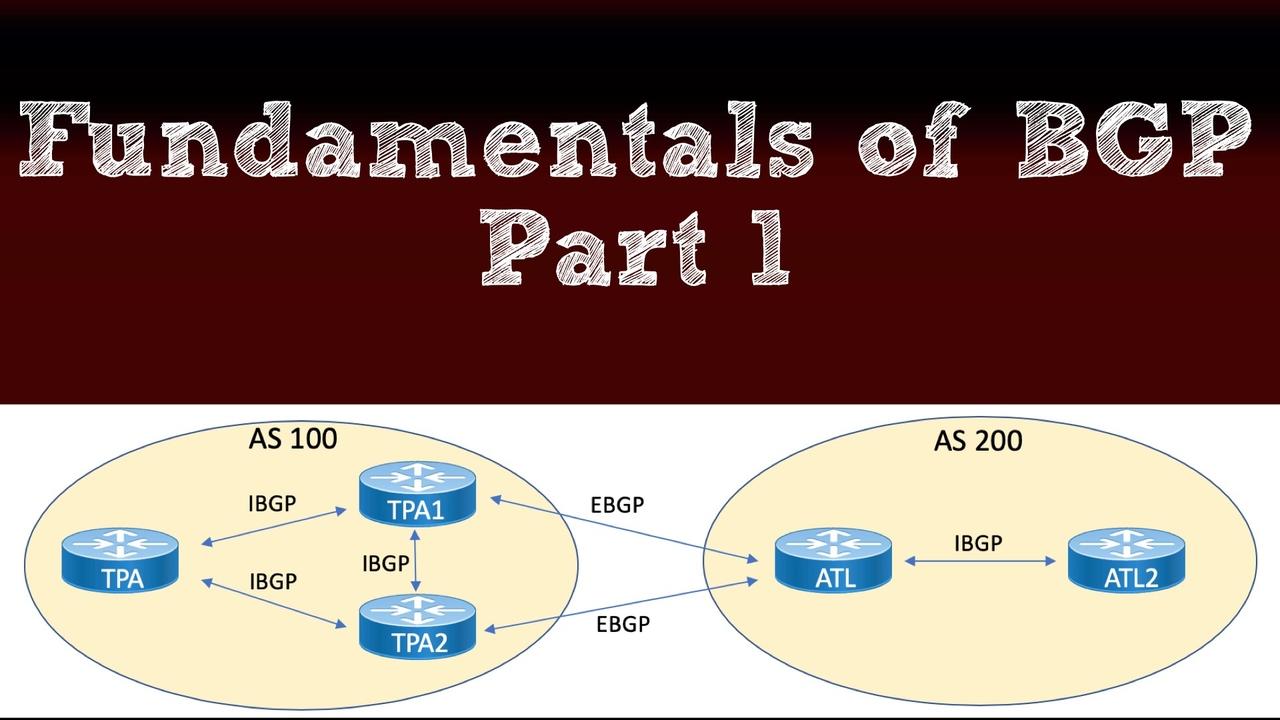
Part 1 of our blog series on Border Gateway Protocol (BGP) gave you an overview of BGP and then delved into BGP message types and neighbor states. Now, in this post, you'll learn about one of...
One of the most intimidating topics for Cisco certification candidates in the Route/Switch track is Border Gateway Protocol (BGP). To help remove the FUD (Fear, Uncertainty, and Doubt) surrounding...
I recently returned from the Cisco Live US 2018 event in Orlando, Florida. It was a great experience, with lots of conversations, sessions, and insight. You can expect more content about what I...
In this new video, you'll learn the need for wireless LAN (WLAN) security, along with multiple approaches and protocols for better securing your wireless LANs.
Topics include:
- War Driving
- MAC...
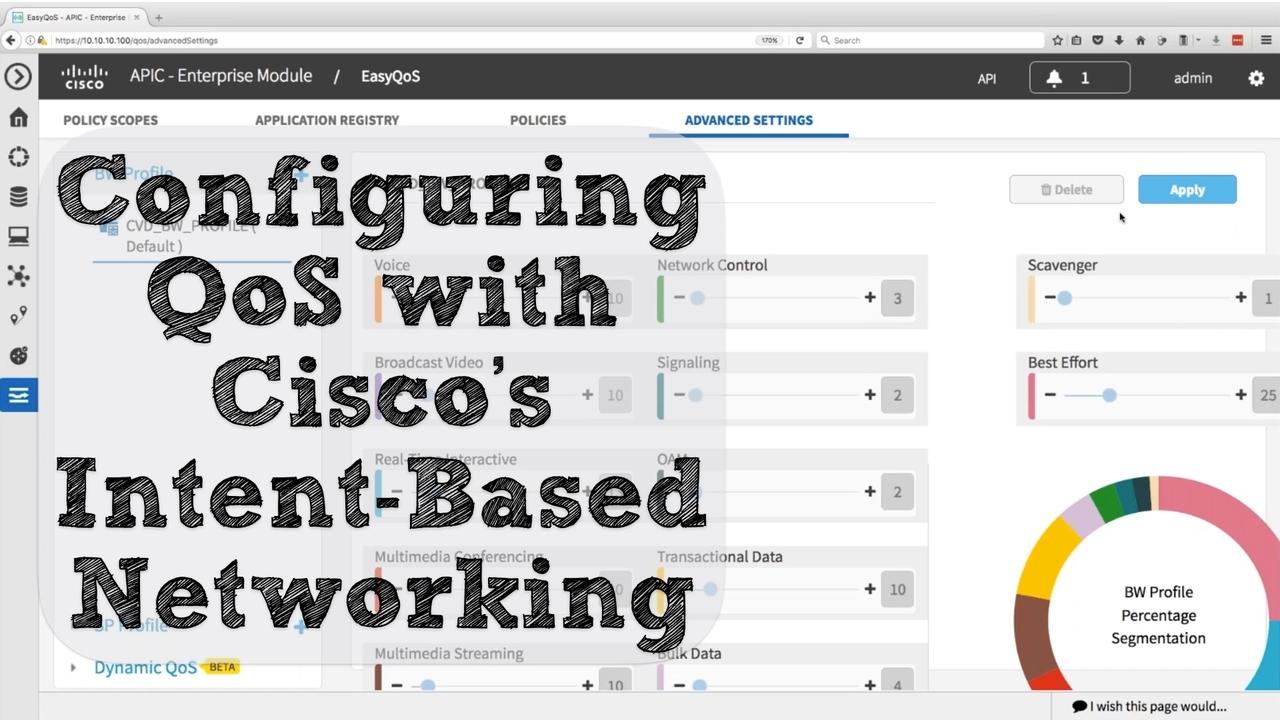
Over the past few months, you might have noticed Cisco’s publicity push regarding intent-based networking. The first time I saw this new brand messaging was at the Las Vegas McCarran...
Last week (on Cyber Monday), I did a webinar covering the theory and configuration of multiple QoS mechanisms. Here's what you'll learn in this replay of that webinar:
- Learn QoS Mechanisms
- ...
I recently did a Facebook Live session covering 5 major Software Defined Networking (SDN) concepts. If you missed the live session, or just want to watch a replay, check out this video.
We...
The Need to Know MQC in a World of Automation
These days, Quality of Service (QoS) can be configured relatively easy. If we’re using the APIC-EM as a network controller to manage our routers...
The Auto Smartports feature available on Cisco Catalyst switches allows a port to automatically detect that you’ve attached a device it can recognize (e.g. a Cisco IP Phone, wireless access...
Some of my blog posts (most of them, in fact) focus on teaching you some technical content or offer career advice. But, sometimes, I just need to share a major milestone with you. That’s...
Studying for your CCNA R/S (200-125) exam? If so, a perusal of the exam topics list can be daunting. Clearly, you’re going to spend a significant amount of time getting at least a passing...
The day-to-day tasks of Cisco network engineers are in the midst of a major industry shift. Specifically, we’re moving away from traditional command line interface (CLI) commands, and...
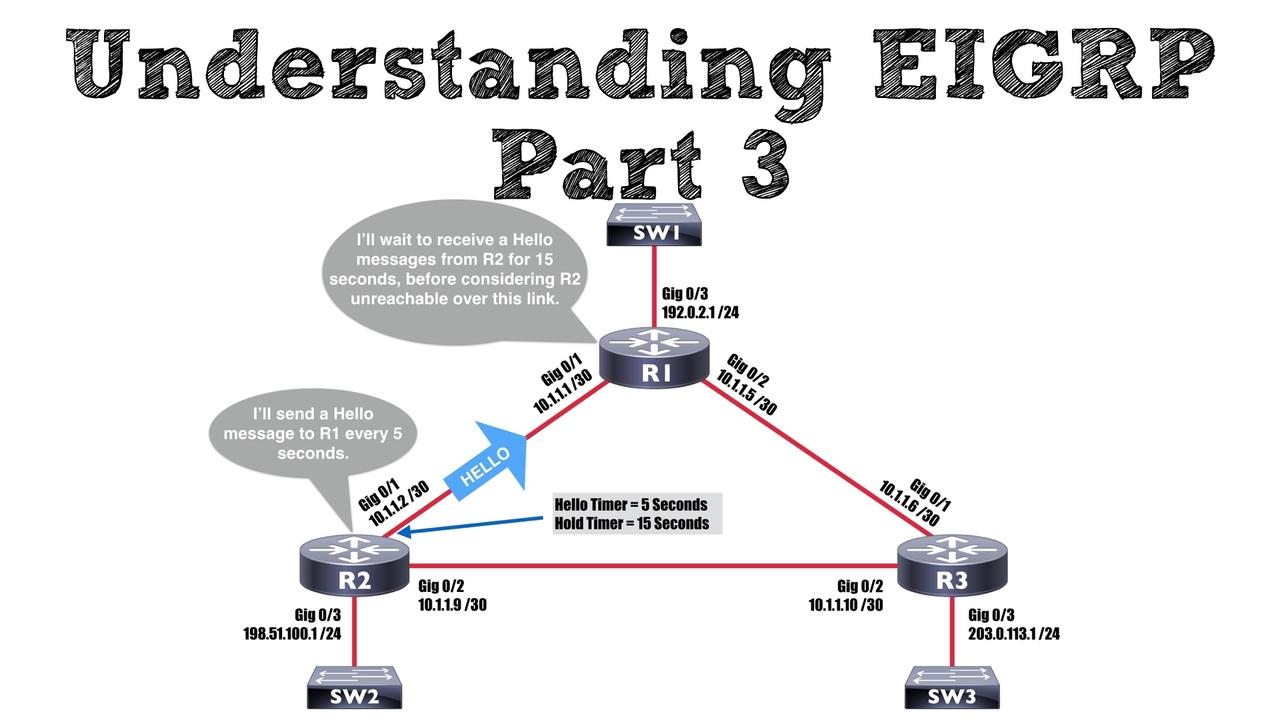
This blog post wraps up our series on Understanding EIGRP by discussing two final topics:
- The EIGRP Router ID
- EIGRP's Neighborship Requirements
Let's begin our discussion by considering the...
Typically, an EIGRP-speaking router dynamically discovers its neighbors, by sending multicast Hello messages. However, there is an option to statically configure those neighbors, and communicate...
It's another one of those buzzwords we're hearing a ton these days, the Internet of Things, or IoT for short.
But what exactly is it, and how's it going to impact us as networking professionals?...
Sometimes, we might want a router interface to participate in an EIGRP routing process (in order to advertise that interface's network) without that interface sending out EIGRP Hello messages....
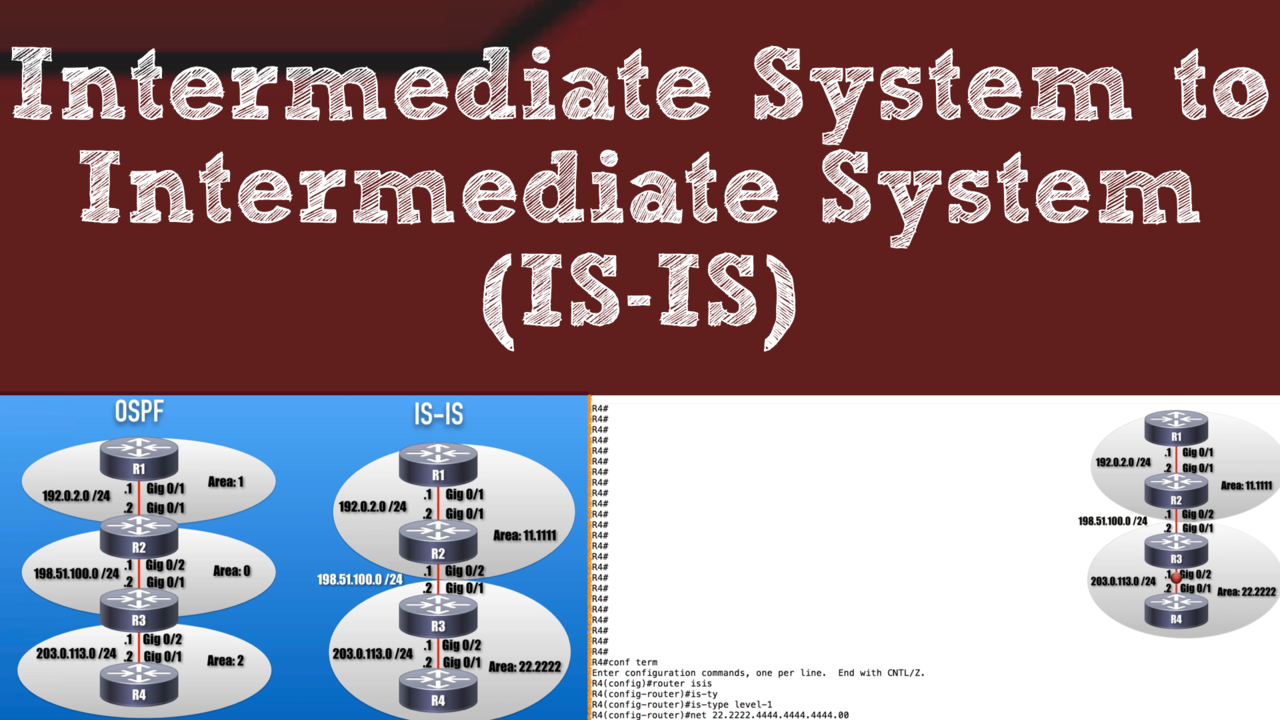
In our Cisco routing and switching studies, we commonly study routing protocols such as RIP, OSPF, EIGRP, and BGP. However, there's a very scalable, fast converging, link-state routing...
Once of EIGRP’s claims to fame is its fast convergence in the event of a link failure. However, one thing that might slow down this convergence is timer configuration. That's the focus of...

In the first blog post in our Understanding EIGRP series, we were introduced to EIGRP’s features, in addition to a basic configuration example, and a collection of verification commands....

I used to work as a Network Design Specialist at Walt Disney World, in Florida. Their massive network contained over 500 Cisco routers (and thousands of Cisco Catalyst switches). What was the...
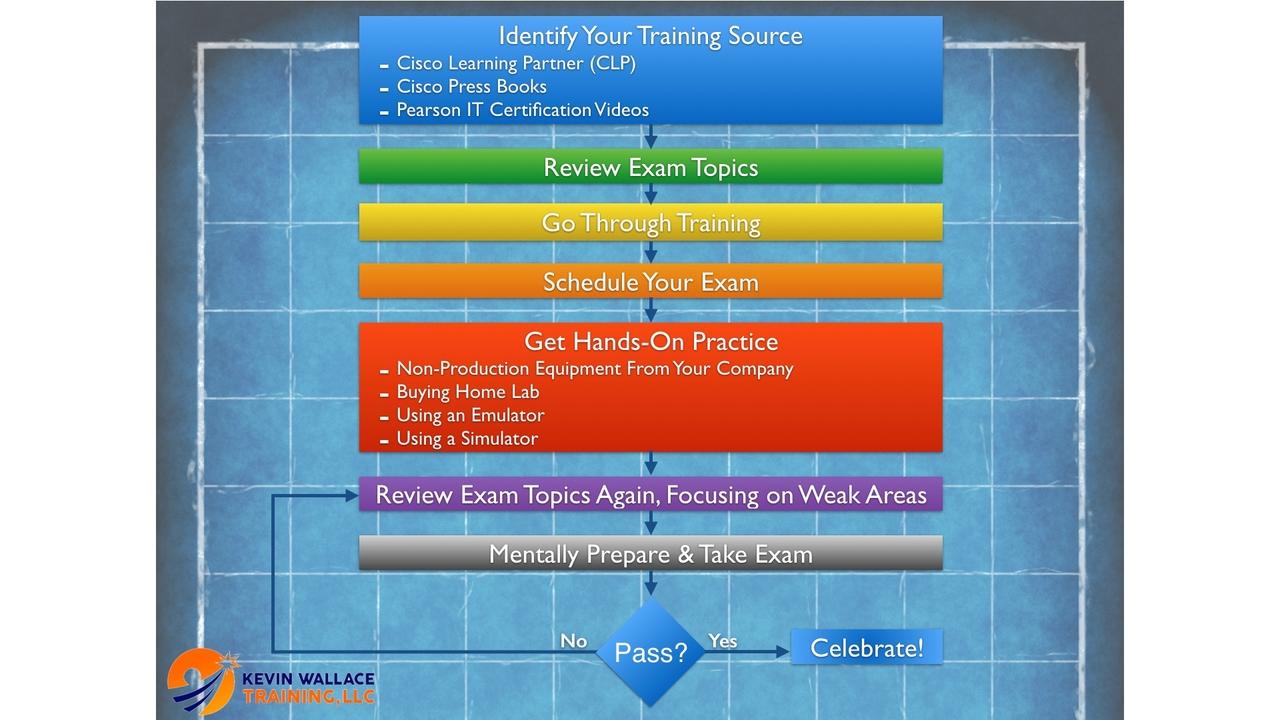
You want to get your first (or next) Cisco certification, but do you have a specific preparation strategy, or are you just winging it? If you do have a structured framework you’re confidently...
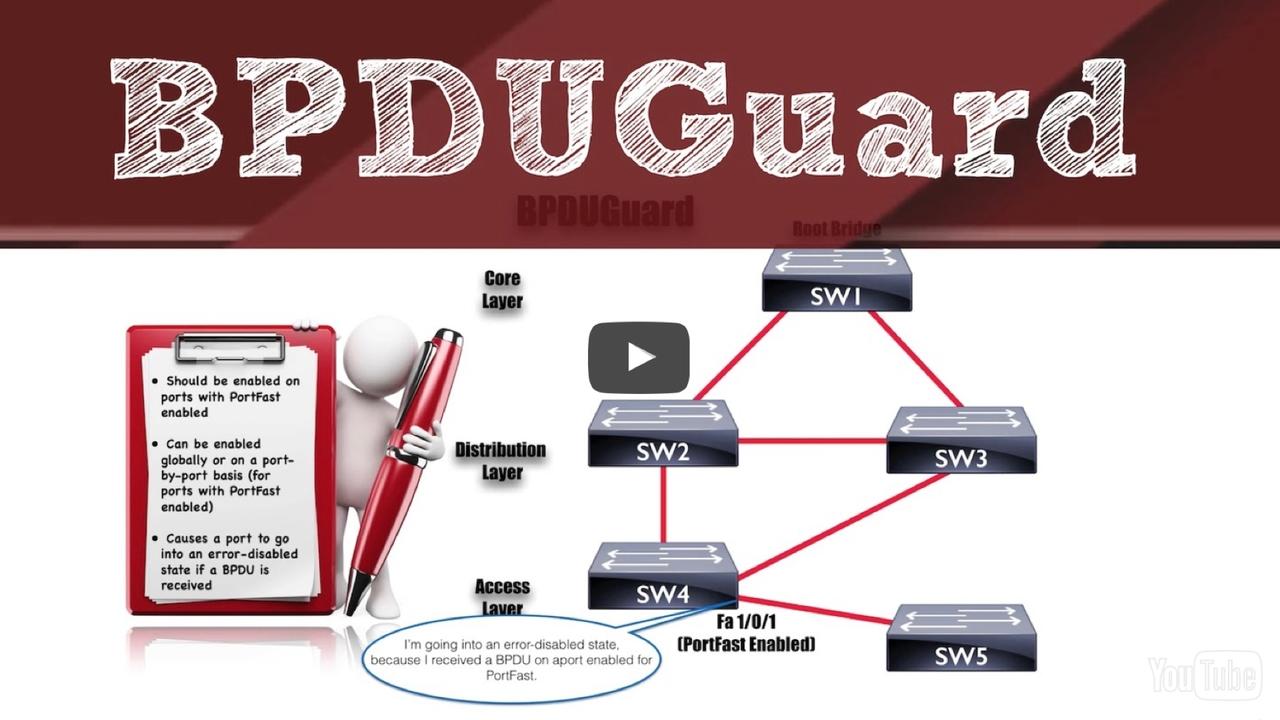
Yet another new topic on the new CCNA R/S v3 exam is BPDUGuard, which is an enhancement to Spanning Tree Protocol (STP) available on our Cisco Catalyst switches. Specifically, BPDUGuard can help...
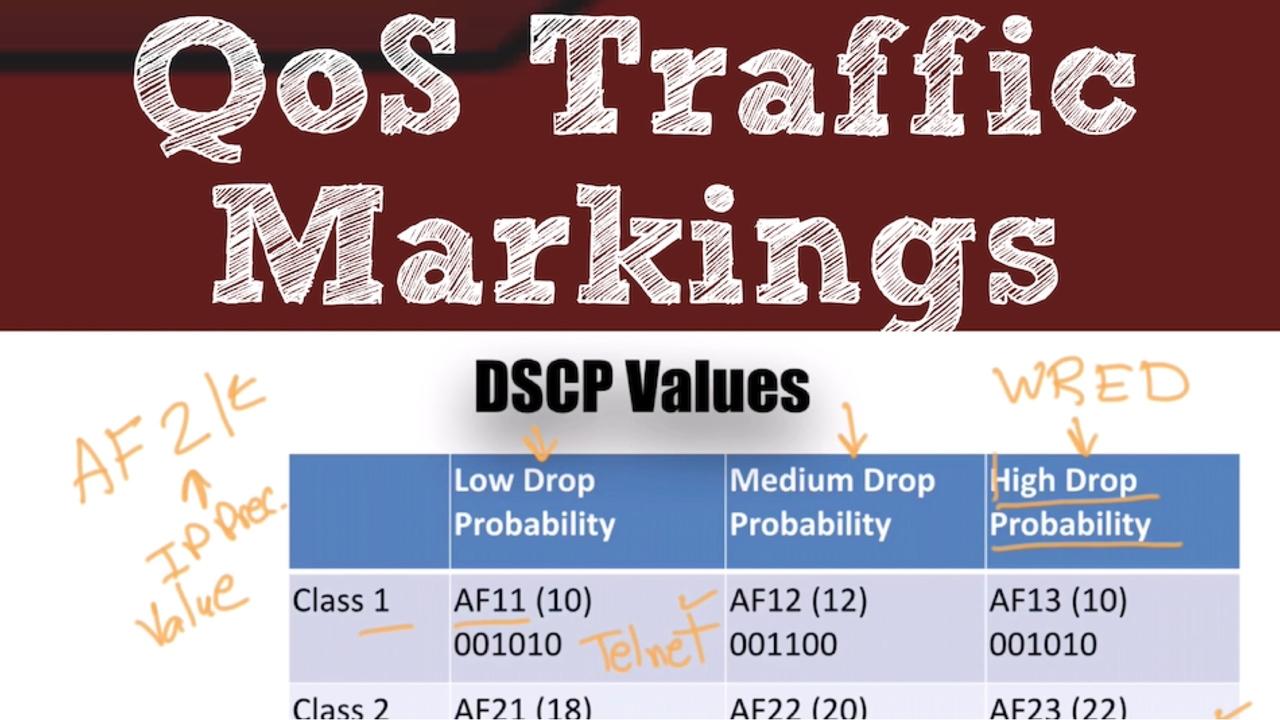
One of the new topics on the new CCNA R/S v3 exam is Quality of Service (QoS). Having taught QoS for many years, I’ve noticed that one of the topics students find most challenging is QoS...

The recently announced CCNA R/S version 3 includes a collection of topics falling under the category of Network Programmability. The underlying technology here is Software Defined Network (SDN),...
A Wide Area Network (WAN) is a network with geographically separate locations, and these locations can be interconnected in a variety of topologies. This video shows you the three WAN topologies...
The new CCNA R/S version 3 exam requires you to know how to configure static routing, for both IPv4 and IPv6 networks.
This video, which is a sample from my upcoming CCNA R/S v3 Complete Video...
For me, the addition of QoS to the list of topic areas for the new CCNA R&S version 3 exam was a great thing. The reason is, QoS is my absolute favorite Cisco topic. So, I couldn’t wait...
In this video we’re covering the fundamental concepts surrounding the IP, ICMP, UDP, and TCP networking protocols. Having a solid understanding of these protocols is critical to just...
An IPv6 address is 128 bits in length, and like an IPv4 address, it’s divided into prefix bits (representing the network segment) and host bits (uniquely identifying a host on that network...
How do you get hands-on experience when you’re preparing for your CCNA R/S or CCNP R/S certifications? One option is using the Cisco Learning Labs. You can check out my review here.
Links to...
This video identifies the need for Quality of Service (QoS) and gets you acquainted with several QoS tools.
This video is a sample from my new CompTIA Network+ (N10-006) Complete Video Course, and...