VLAN Security Concepts
Nov 13, 2018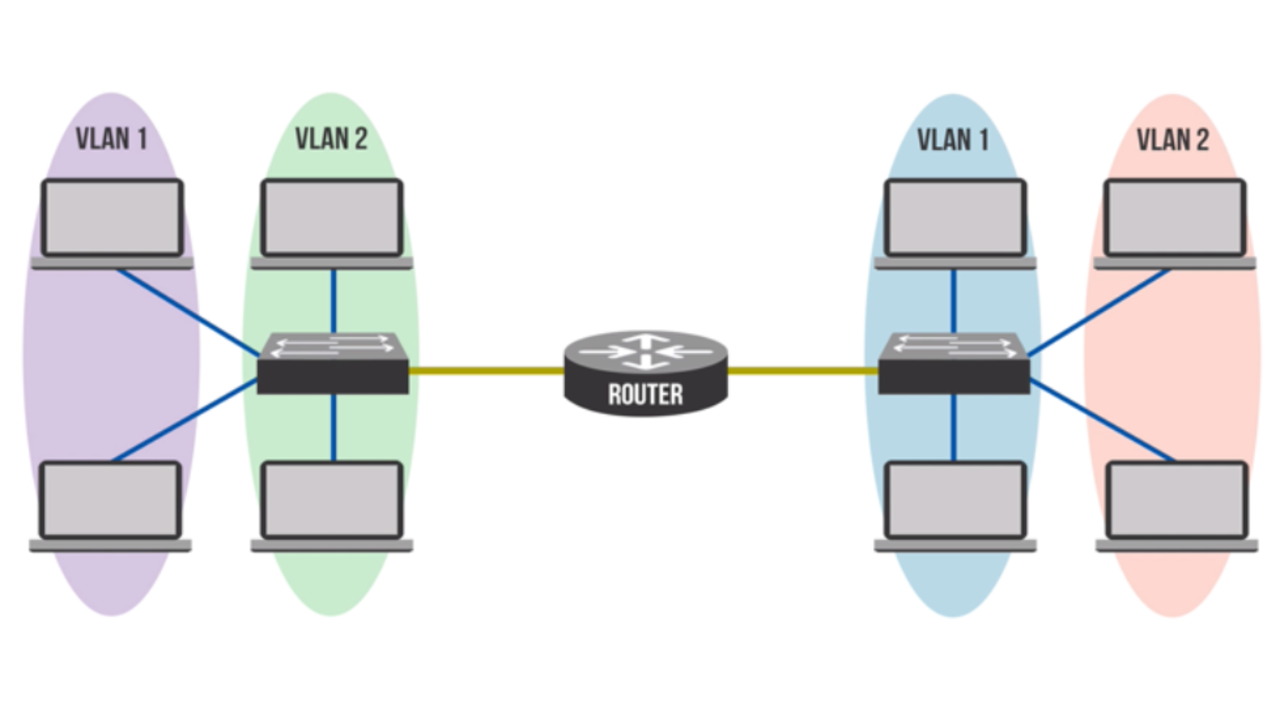
A Virtual Local Area Network (VLAN) is a logical grouping of devices on one or more LANS, configured to communicate as if they were on the same segment. In order to communicate with devices in another VLAN, a Layer 3 device must be present for routing.
Private VLAN (PVLAN)
One way to simplify a multi-VLAN deployment is by use of the Private VLAN (PVLAN) feature. PVLANs achieve isolation at Layer 2 between ports in the same VLAN. This is done by designating the ports as one of three types: promiscuous, isolated, orcommunity. Each designation has its own unique set of rules which regulate the ability to communicate with other devices in the same VLAN.
Promiscuous Ports: These ports have the ability to communicate with all other ports within the PVLAN. The default gateway for the network segment would likely be a promiscuous port, since all devices need to be able to communicate with the gateway.
Isolated Ports: These ports have Layer 2 separation from all other ports within the PVLAN, except for promiscuous ports. A PVLAN will block all traffic to an isolated port, except the traffic originating from a promiscuous port. A common example is a hotel or university network, where end users would have Internet access but no access to other clients.
Community Ports: These ports are able to communicate among all other community ports, as well as promiscuous ports. Many enterprise networks will contain community ports, allowing clients to communicate directly with other internal devices such as database or email servers.
Each of these port types are also associated with specific VLAN types, which work together with the port designations to create a PVLAN structure.
- Primary VLAN: The primary VLAN carries traffic from the promiscuous ports to all other ports in the same VLAN.
- Isolated VLAN: The isolated VLAN is a secondary VLAN that carries traffic from isolated ports to promiscuous ports.
- Community VLAN: The community VLAN is also a secondary VLAN and carries traffic among community port members. It’s also responsible for traffic going from community ports to promiscuous ports.
Native VLAN
The Native VLAN is simply the untagged VLAN on an 802.1q trunked switchport. The 802.1Q protocol provides a way for ethernet frames to be tagged with specific VLAN identifiers. Any untagged frames arriving on a trunk port are assumed to be a member of the Native VLAN.
When configuring a trunk port, the Native VLAN should be set to the same value on each end in order to avoid Spanning Tree Protocol (STP) loops. By default, the native VLAN is set to VLAN 1. A recommended best practice is to change the Native VLAN to another unused VLAN where no hosts or other devices reside. This is done in order to avoid VLAN hopping attacks such as double-tagging.
It’s easy to confuse the ideas of the Native VLAN and the Default VLAN. Just to provide clarity about these terms, the following can be stated:
- The default VLAN will always be VLAN 1. This is determined by Cisco and cannot be changed. The default VLAN assignment for an access port will always be VLAN 1, unless otherwise specified.
- In the same way, the default Native VLAN value will always be VLAN 1, as determined by Cisco. If the Native VLAN value is not changed, this defaults to VLAN 1.
- The Native VLAN can be changed to any value, even though by default it is set to VLAN 1. As already stated, it is a recommended best practice to change the Native VLAN to another non-default value for security reasons.
A few other recommended best practices in regard to VLAN security includes the following:
- Shutting down unused interfaces and placing them in a so-called “parking lot” VLAN. This is essentially an unused VLAN where no other clients reside.
- Restrict the VLANs allowed on trunk ports to only those that are necessary.
- Manually configure access ports with the switchport mode access
- Disable Cisco Dynamic Trunking Protocol (DTP) in order to prevent unauthorized trunk link negotiation.


